Privacy Concerns as Smoke Alarm Service Provider Leaves Nearly 1M Documents Exposed Online

Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to vpnMentor about a non-password protected database that contained over 700k documents belonging to Australia’s largest smoke alarm installation and service provider.
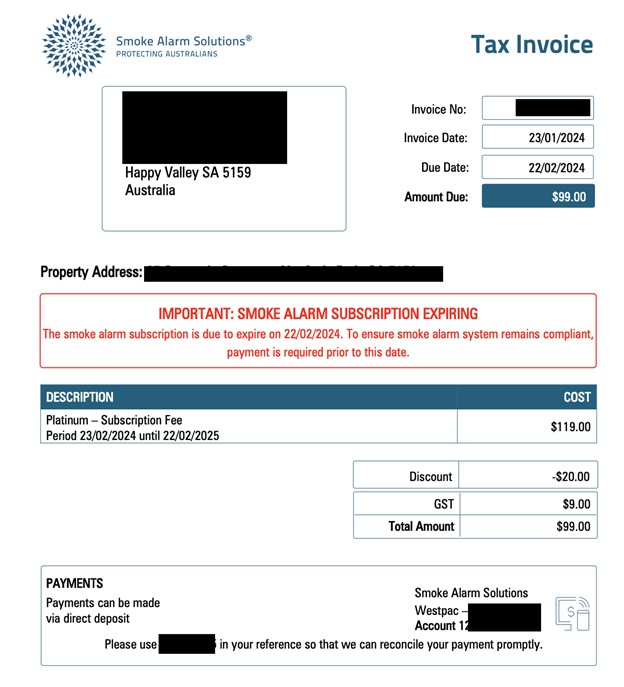
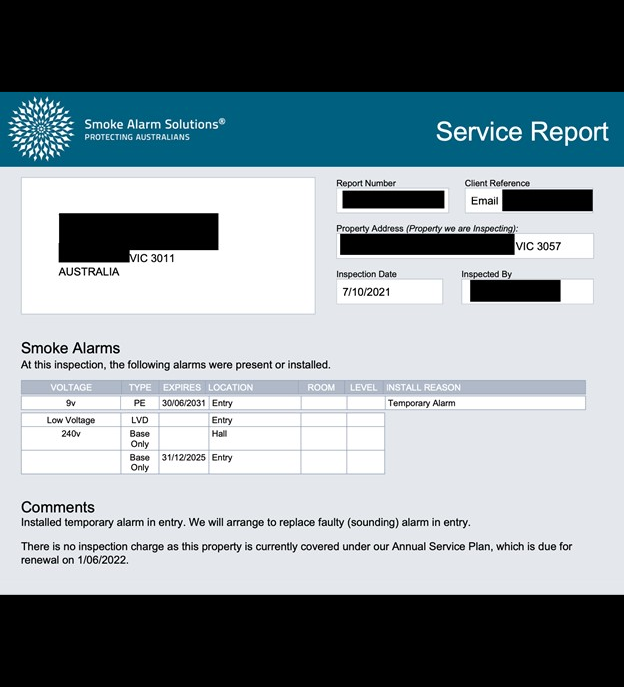
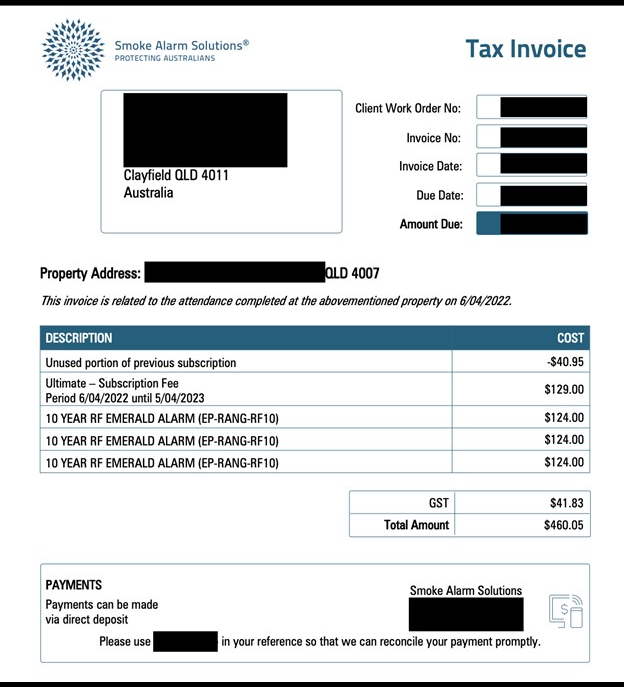
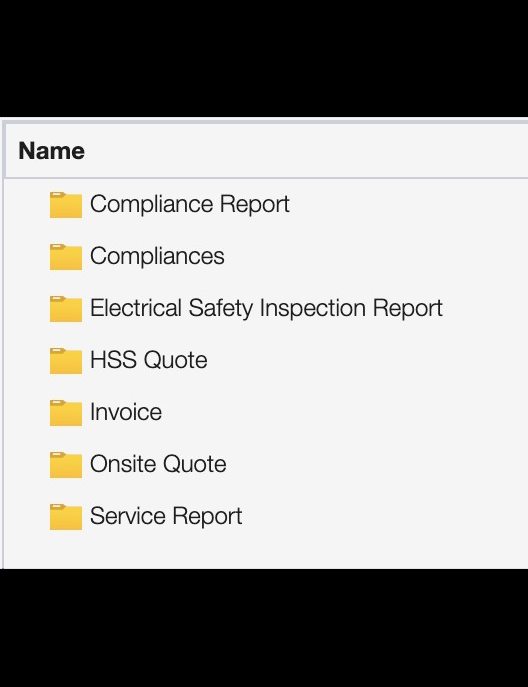
The exposed database contained 762,856 documents and totaled 107 GB. Upon further research, it was indicated that the data belonged to Smoke Alarm Solutions, an Australian company specializing in the installation and maintenance of smoke detectors. The publicly exposed files contained customer information, including detailed invoices, records of inspections, estimates, compliance reports, electrical safety inspections, service quotes, and service reports. The publicly accessible documents provided a comprehensive view of the company's transactions and customer interactions. The database contained 355,384 documents marked as invoices, dated 2021-2024. This number gives a basic idea or estimate of how many individuals could be potentially affected by the exposure. Additionally, there were 24,632 documents marked as “on site quotes” that contained the names and email addresses of the business, agent, or individual obtaining a quote. In a limited sample and manual review of the exposed database, I didn’t see any duplicate documents or information — the documents appeared to be unique.
I immediately sent a responsible disclosure notice to Smoke Alarm Solutions and the database remained open to public access. I received a reply from a technology consultant representing the company that read; “We are aware of this data store. Its state is the unfortunate side effect of some work by a previous system integrator. We are actively migrating to a new customer management platform. We will block all access (or more likely, decommission) this data store as soon as we have migrated the data to our new platform”. However, the records were still accessible nearly 2 months after my first responsible disclosure notice. I sent numerous followup emails including official support links to information on how to restrict public access to the database and finally the database was secured. It is unclear how long the documents were exposed or who else may have gained access to them. Only an internal forensic audit conducted by Smoke Alarm Solutions could identify this information.
In Australia, all properties are legally required to have smoke alarms installed on every level of a home. This includes owner-occupied homes, rental properties, relocatable homes, caravans, camper-vans, or any other residential buildings. The market size of the Fire and Security Alarm Installation Services industry in Australia was estimated to be $4.0bn in 2023. Companies like Smoke Alarm Solutions offer subscription services to help private individuals, landlords, and real estate companies stay compliant with the law. A unique dynamic arises anytime customers are using a service or a product that is legally required, as it typically involves a regulated market. As such, it’s important that these companies provide a high-quality service, which includes safeguarding their consumers’ data to the best of their ability.
According to their LinkedIn page, “Smoke Alarm Solutions is the leading provider of residential smoke alarm compliance and maintenance services to the Australian real estate industry. Australian owned and operated since 2007 with local technicians and electricians located throughout Queensland, Victoria and South Australia”.
Potential Privacy Risks
The invoices and other internal documents contained customer information that could have potential real-world risks if these documents were to inadvertently fall into the wrong hands. According to data from the FBI, in the United States, social engineering accounts for 98% of all cyber-attacks. The Australian Cyber Security Centre offers valuable information, but does not provide statistics of social engineering. On April 4th the ACCC issued an advisory urging citizens to be aware of invoice scams where criminals send victims altered payment requests. The advisory also indicates that in 2023 Australians reported losing $16.2 million to payment redirection scams. As a result of this exposure, detailed information about individuals and their properties was available to anyone with an internet connection, as it was not password protected. In any data exposure, criminals could potentially use privileged knowledge to craft convincing emails, physical mail, or phone calls posing as a representative of the affected company to trick individuals into revealing more personal information or engage in sophisticated phishing attacks using social engineering.
The work report documents exposed sensitive details that only Smoke Alarm Solutions, the installer, and the customer would know, thereby increasing the likelihood of trust for any request for additional information. Hypothetically, criminals could contact the property owner and reference the locations of alarms, installation date, invoice numbers, subscription plans, name of the technician, inspector, and other internal details to gain access to the property for criminal activities. Another potential risk would be the alteration of an invoice to falsely claim there is an outstanding payment due and attempt to receive money, credit card data, or banking information.
In addition to the online risks, this information could be potentially exploited for non-digital criminal activity, such as burglary or vandalism. Inspection records and estimates could provide insights into the structure and layout of homes and businesses, allowing criminals to potentially identify vulnerable properties. One extreme hypothetical example would be a criminal posing as a service technician who claims to be checking a faulty alarm, thus gaining physical access to a property for nefarious purposes. I am not saying or claiming that any customer of Smoke Alarm Solutions is at risk of any fraudulent activity or social engineering attempts. I am only discussing real-world examples of potential risks and possible scenarios that consumers should be aware of.
I highly recommend that companies who collect and store data implement cybersecurity and data protection measures. This includes encrypting sensitive data, running regular security audits, and training employees to raise awareness about cybersecurity threats. As consumers, protecting ourselves from scams is now almost a part of our daily routine. When criminals use insider information or pretend to represent a company that consumers have a business relationship with, it makes it even harder to identify scams and covert attacks. My advice to anyone who receives suspicious communications or invoices is to always verify that these are legitimate. Here are a few steps to consider before sharing your personal information via phone or email:
- Verify the communication.
If you receive an unexpected call, email, or message from a company claiming to be one you've done business with, verify their identity. Use official contact information from the company's website or any previous communication you have had with them and not the contact method where you received the suspicious message. - Never share sensitive information.
Do not give your personal or financial information over the phone, email, or messages unless you know for certain who you are giving it to. Remember that most legitimate companies will not typically ask for sensitive information via email or unsolicited phone calls. You can always ask to call the person back using an official phone number. Help prevent others from being scammed by reporting any suspicious emails, messages, or calls to the company being impersonated. - Remember it’s ok to ask questions and trust your suspicions.
If something doesn't feel right, it’s always better to be safe than sorry. Look for common signs of a scam, such as spelling and grammatical errors, or urgent demands for immediate action. Always be cautious if the communication seems overly aggressive, threatening, or manipulative. Educate yourself on how common scams and phishing techniques work and the tactics scammers use. The threat landscape changes daily but everyone should know the basics.
I have published my findings only after the database was restricted from public access to protect the privacy of potentially affected individuals. The law firm representing Smoke Alarm Solutions has stated “Based on the circumstances of the alleged incident as instructed by our client, the alleged incident does not, in our view, constitute a notifiable data breach under the Act, and therefore our client is not required to notify either the authorities or any individual about such alleged incident”.
According to the Privacy Act of 1988 and the Australian Privacy Principles (APPs) ‘Personal information’ is defined as any information or an opinion about an identified individual, or an individual who is reasonably identifiable. Common examples are an individual’s name, signature, address, telephone number, date of birth, medical records, bank account details, employment details and commentary or opinion about a person. I am not claiming that this is an identifiable data breach under Australian law, I am only promoting personal privacy and data protection. I believe that customers should always have a choice in how their information is publicly shared. It is not up to me to decide what is a violation of APPs, what constitutes a data breach, or a personal privacy concern for Australian citizens. I do believe that individuals should be aware in the event that a company has exposed documents such as invoices or other files online that contain their basic PII (accidentally or purposely).
As an ethical security researcher, I never download the data I discover, and take a limited number of screenshots for verification purposes. It is unknown if anyone else accessed these records or how long they were publicly exposed. I am not implying any wrongdoing by Smoke Alarm Solutions nor am I implying that their customers, technicians or installers ever were at risk. I only state the facts of the discovery, how this information could potentially be misused, and the associated hypothetical risks. In my research I always maintain a neutral stance, I report only facts of the discovery, give general advice intended for data security and personal privacy. My reporting is intended for educational purposes and in no way intended to be misleading or defamatory and I make no claim that customers are at risk of any form of social engineering or breach of personal privacy.